<< Назад на страницу выбора модели

| Firewall throughput (1518bytes) | 40 Gbit/s |
| IPS throughput | 15 Gbit/s | |
| IPS+AV throughput | 13 Gbit/s | |
| Concurrent sessions | 12,000,000 | |
| New sessions per second | 400,000 | |
| VPN Throughput (IPSec, AES, 1420 byte) | 18 Gbit/s | |
| Virtual firewalls | 1000 | |
| MTBF | 19.18 years | |
| MTTR | 3.13 min | |
| Maximum power | 700 W | |
| DC power supply | -48 V to -60 V | |
| AC power supply | 100 V to 240 V | |
| Fixed port | 4 x 10GE+16GE+8SFP | |
| Expansion Slots | 5 x WSIC | |
| Interface module | WSIC: 2 x 10GE (SFP+)+8 x GE (RJ45), 8 x GE (RJ45), 8 x GE (SFP), 4 x GE (RJ45) BYPASS | |
| Height | 3U | |
| Dimensions (W×D×H) | 442mm×470mm×130.5mm | |
| Weight (full configuration) | 24 kg | |
| HDD | Optional. Supports 300 GB hard disks (RAID1 and hot swappable). | |
| Redundant power supply | Standard configuration | |
| Operating environment | Temperature: 0°C to 40°C/5°C to 40°C (with optional HDD) Humidity: 10% to 90% | |
| Non-operating environment | Temperature: -40°C to 70°C Humidity: 5% to 95% | |
| Software certifications | ICSA Labs: Firewall, IPS, IPSec, SSL VPN CC: EAL4+ NSS Labs: Recommended Rating | |
| Hardware cerifications | CB, CCC, CE-SDOC, ROHS, REACH&WEEE(EU), C-TICK, ETL, FCC&IC, VCCI, BSMI |
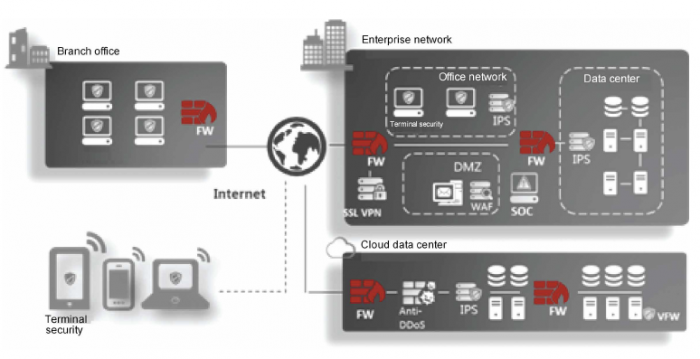
| Function | Description |
| Context awareness | ACTUAL (Application, Content, Time, User, Attack, Location)–based awareness capabilities Eight authentication methods (local, RADIUS, HWTACACS, SecureID, AD, CA, LDAP, and Endpoint Security) |
| Application security | Fine-grained identification of over 6000 application protocols, application specific action, and online update of protocol databases Combination of application identification and virus scanning to recognize the viruses (more than 5 millions), Trojan horses, and malware hidden in applications Combination of application identification and content detection to identify file types and sensitive information to prevent information leaks |
| Intrusion prevention | Provides over 5000 signatures for attack identification. Provides protocol identification to defend against abnormal protocol behaviors. Supports user-defined IPS signatures. Supports APT defense. Interworking with the Sandbox to detect and block the malicious files in the network. |
| Web security | Cloud-based URL filtering with a URL category database that contains over 130 million URLs in over 80 categories Defense against web application attacks, such as cross-site scripting and SQL injection attacks HTTP/HTTPS/FTP-based content awareness to defend against web viruses URL blacklist and whitelist and keyword filtering |
| Email security | Real-time anti-spam to detect and filter out phishing emails Local whitelist and blacklist, remote real-time blacklist, content filtering, keyword filtering, and mail filtering by attachment type, size, and quantity Virus scanning and notification for POP3/SMTP/IMAP email attachments |
| Data security | Data leak prevention based on content awareness File reassembly and data filtering for more than 30 file types (including Word, Excel, PPT, and PDF), and file blocking for more than 120 file types |
| Security virtualization | Virtualization of security features, forwarding statistics, users, management operations, views, and resources (such as bandwidths and sessions) |
| Network security | Defense against more than 10 types of DDoS attacks, such as the SYN flood and UDP flood attacks VPN technologies: IPSec VPN, SSL VPN, L2TP VPN, MPLS VPN, and GRE |
| Routing | IPv4: static routing, RIP, OSPF, BGP, and IS-IS IPv6: RIPng, OSPFv3, BGP4+, IPv6 IS-IS, IPv6 RD, and A CL6 |
| Working mode and availability | Transparent, routing, or hybrid working mode and high availability (HA), including the Active/Active and Active/Standby mode |
| Intelligent management | Evaluates the network risks based on the passed traffic and intelligently generates policies based on the evaluation to automatically optimize security policies. Supports policy matching ratio analysis and the detection of conflict and redundant policies to remove them, simplifying policy management. Provides a global configuration view and integrated policy management. The configurations can be completed in one page. Provides visualized and multi-dimensional report display by user, application, content, time, traffic, threat, and URL. Enterprise administrators can perform assessment over the current network security status by the network security report and providing the related optimization suggestions. |
